Web applications that allow file uploads may have a file upload vulnerability that lets an attacker upload a file with a malicious name.
An attacker may upload a file with a malicious file name to execute arbitrary code on the server or do other harm using this vulnerability.
The file may be submitted as an image if the web application just validates the file extension. Since the file name contains “.php,” an attacker may access the file by adding “.php” to the URL, which causes the server to run the file as PHP code. This may provide the attacker server control or sensitive data.
If the web application permits uploading files with any extension and the attacker uploads “file.php” and renames it to “file.php; rm -rf /,” the server will execute the command after the semicolon (;) and destroy all files.
Hackers may also upload malicious JavaScript or HTML files.
File upload vulnerability instances such as these can prove highly detrimental and lead to tampering and loss of sensitive data.
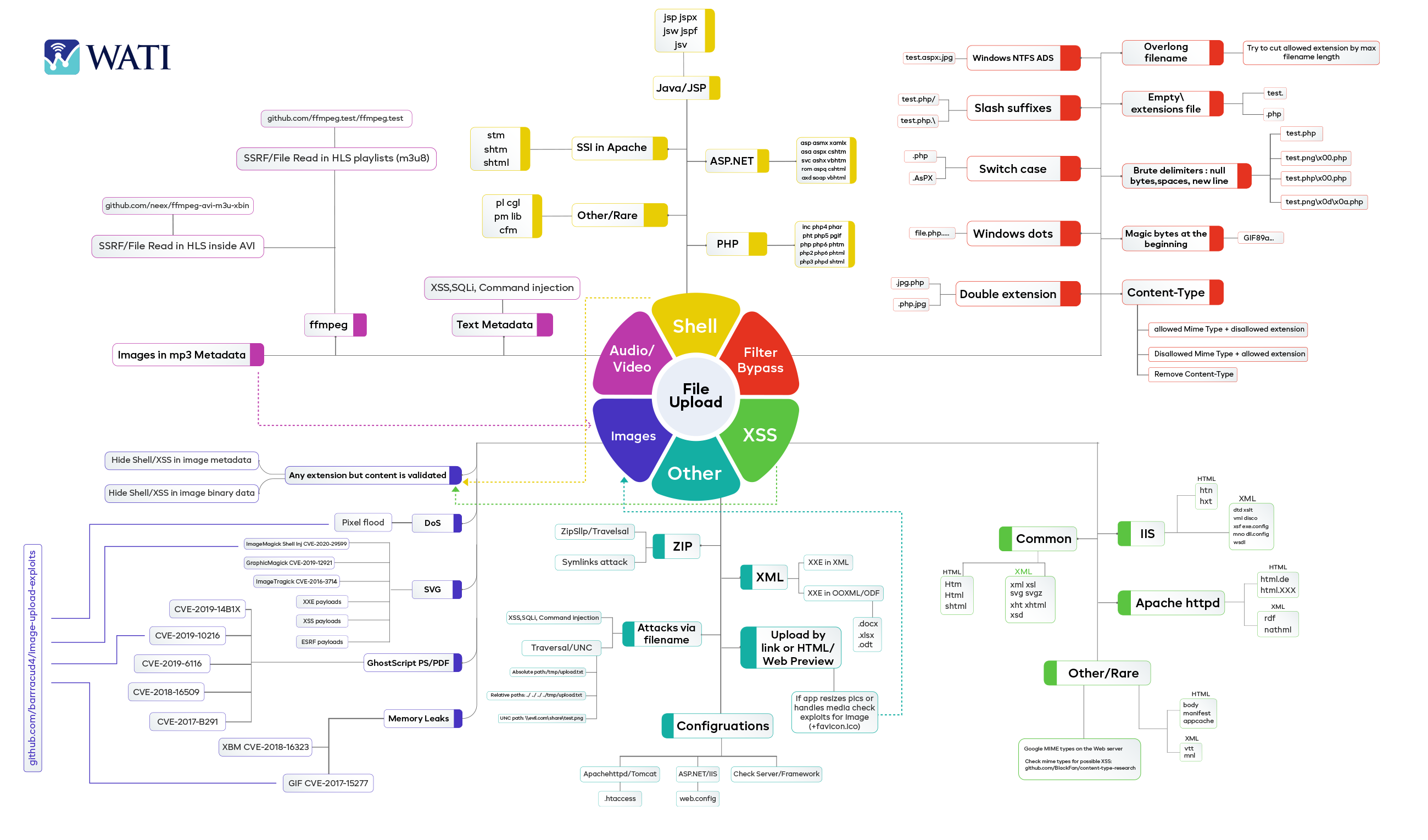
ABUSED FILE TYPES
Several misused file formats may exploit web application file upload vulnerabilities. Examples of malicious file upload vulnerabilities include:
- Server-executable script files: PHP, ASP, and JavaScript. These files allow server code execution and system control.
- Microsoft Word and Excel files may include harmful macros or scripts. These files may run arbitrary code on client machines.
- PHP file upload vulnerability may occur when image files i.e., GIF or PNG files with PHP scripts might contain concealed harmful malware.
- Archive files, like zip or rar files, may transmit many malicious files.
- Audio and video files: MP3 and mp4 files may transmit malicious payloads or conceal harmful material in their metadata.
BYPASSING METHODS
There are several ways an attacker can try to bypass and exploit file upload vulnerability in a web application, including:
- File name manipulation: An attacker can try to upload a file with a malicious file name that can be used to execute arbitrary code on the server or to cause other types of damage.
- File type manipulation: An attacker can try to upload a file with a different file extension that is not properly validated by the application, such as a PHP file disguised as an image file.
- File content manipulation: An attacker can try to upload a file that contains malicious code, such as a script that can be used to execute arbitrary code on the server.
- File size manipulation: An attacker can try to upload a large file that exceeds the maximum file size limit set by the web application, which can cause a buffer overflow or other types of vulnerabilities.
- File inclusion: An attacker can try to include a file from the local file system by exploiting the file inclusion vulnerability.
- File Tampering: This type of attack occurs when an attacker is able to modify an existing file on the server. This can be done by exploiting a file upload vulnerability or by guessing the name of an existing file.
DEMONSTRATION
An attacker may circumvent a web application file upload vulnerability in numerous ways:
- File name manipulation: An attacker may upload a malicious file to execute arbitrary code on the server or do other harm.
- File type manipulation: An attacker may upload a PHP file disguised as an image file.
- File content manipulation: An attacker may upload a file with malicious code, such as a script that executes arbitrary code on the server.
- File size manipulation: An attacker may upload a big file that exceeds the web application’s file size restriction, causing a buffer overflow or other vulnerabilities.
- File inclusion: The file inclusion vulnerability allows attackers to incorporate local files.
- File Tampering: An attacker modifies a server file. Exploiting a file upload vulnerability or guessing a file name may achieve this.
EXPLOITS
Depending on the vulnerability and desired effect, file upload vulnerabilities might employ various payloads. Github file upload vulnerability payloads include:
- An executable or script disguised as a.jpg or.doc file. The attacker may access sensitive data or run malicious code by uploading and executing the file on the server.
- An XSS payload file that may inject malicious code into other users’ web pages.
- An SQL injection payload file that may modify a web application’s database and access sensitive data.
- A file with a command injection payload that lets the attacker run arbitrary server instructions.
- A file with a Remote Code Execution payload to execute arbitrary code on the server.
PREVENTION
For file upload vulnerability prevention and strong file upload security, it is important to properly validate and sanitize any user-provided file names before allowing them to be uploaded. Additionally, it is also crucial to maintain secure file upload by storing the uploaded files in a safe location and having proper access controls in place to prevent unauthorized access. Following these file upload security best practices helps keep all kinds of file upload security vulnerabilities at bay.



