Cybersecurity
Implement · Manage · Secure
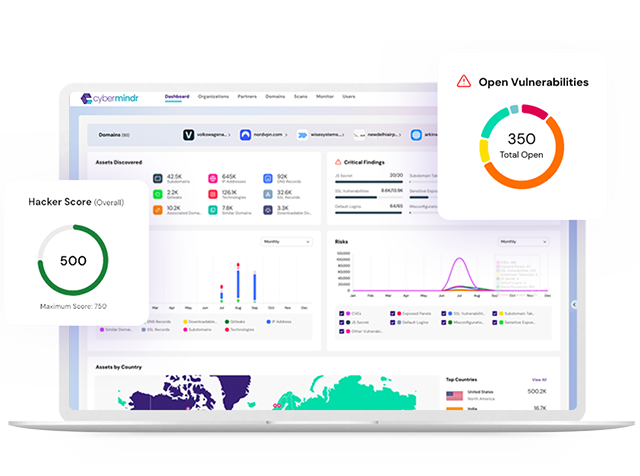
Vulnerability Assessment and Pentesting Services
Simulate high-impact security breaches, before they happen from bad actors, so as to strengthen your organization’s security posture.
We offer Vulnerability Assessment and Penetration Testing (VAPT) for all your digital assets – applications, data, identities, IoT, and digital infrastructure (devices, network, and Cloud). The Security Audit Reports (SAR) are comprehensive and include actionable insights to prioritize the security hardening process.
Cyber Risk & Compliance
Security compliance is not just nice to have, it’s a business necessity for many, to be able to provide peace of mind for employees, clients, and partners.
With standards continuously evolving, compliance can be daunting. WATI provides expertise and guidance as you embark on assessment, audit, and attestation of your chosen certification.
SOC Managed Services
WATI offers SOC-as-a-Service for continuous security monitoring, threat detection, and response management.
Our team of highly-skilled consultants works with technology products you have or choose to cover both proactive and reactive services. Our coverage options are flexible, designed for quick scale, and you can start with as-little or as-much to meet your desired SLAs and business needs.
Cybersecurity Training
It is smart to build Cyber preparedness with employees as front and center of it.
![]()
Secure Coding Practices for Developers
![]()
Cybersecurity Bootcamp for IT Professionals
Even large-scale investments in the technical gear for cyber defense will be ineffective
when employees are not adequately trained on Cyber defenses.
WATI offers two distinct tracks of Cybersecurity training – for developers and all IT professionals.
Cyber Advisory – Maturity Roadmap
Cyber Maturity Roadmap (CMR) delivers actionable guidance to define=>build=>refine your Enterprise Security Initiative.
We work with your teams to develop a multi-year strategy to maximize ROI for investments across products, projects, and people.
Security Team Certifications
WATI’s consultants carry advanced cybersecurity certifications and technical experience for Ethical Hacking, Cybersecurity Compliance and Risk assessments, Cybersecurity Monitoring & Event Analysis, and Cybersecurity Incident Response.