As the digital world continues to expand and evolve, cybersecurity has emerged as a top priority for organizations across various industries. The ever-increasing complexity of technology and the rise of sophisticated cyber threats demand effective security strategies to protect sensitive information. Vulnerability Assessment and Penetration Testing (VAPT) is key to uncovering and addressing potential security flaws. In this detailed guide, we examine the various elements of VAPT, discussing their importance, processes, types, advantages, and beyond.
What is VAPT?
Vulnerability Assessment and Penetration Testing (VAPT) is an essential components of a holistic cybersecurity strategy. These services encompass a range of testing methodologies designed to identify, evaluate, and mitigate security vulnerabilities in an organization’s IT infrastructure.
Vulnerability Assessment (VA): This process involves using automated tools and manual techniques to identify security vulnerabilities. The assessment focuses on discovering weaknesses, such as outdated software, weak passwords, and misconfigurations, that could be exploited by attackers. The outcome is a detailed report highlighting the vulnerabilities, their severity, and recommended remediation measures.
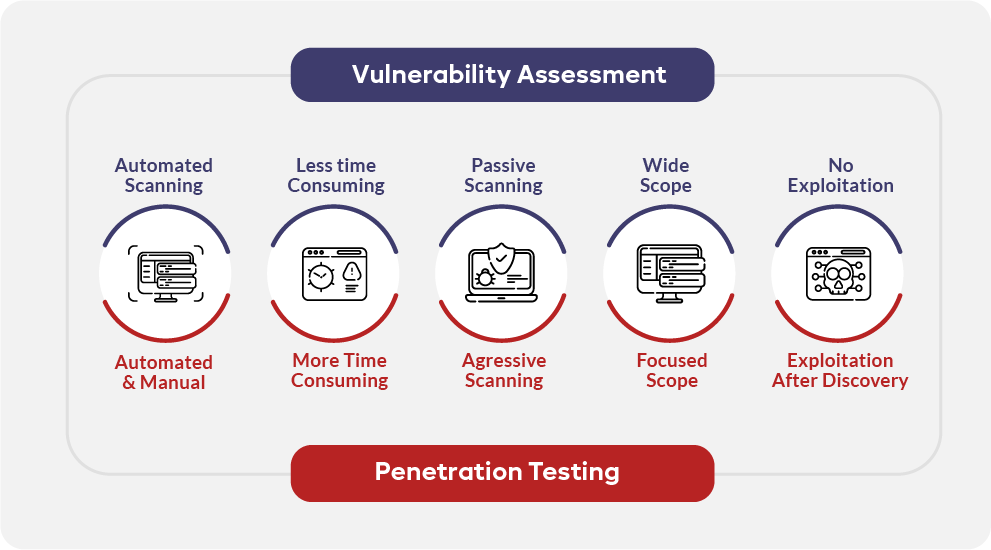
Penetration Testing (PT): Also known as ethical hacking, penetration testing involves simulating cyber-attacks to exploit identified vulnerabilities. Unlike VA, which only identifies weaknesses, PT aims to understand the real-world impact of an attack by actively exploiting vulnerabilities. This hands-on approach helps organizations understand the extent of potential damage, the feasibility of attacks, and the effectiveness of their security measures.
Combining VA and PT offers a comprehensive overview of an organization’s security posture. While VA provides a broad analysis of potential weaknesses, PT offers an in-depth understanding of how these vulnerabilities can be exploited. This dual approach helps organizations prioritize and address security risks effectively.
Why VAPT is Essential for Businesses
The significance of VAPT cannot be overstated in the current cybersecurity landscape. Here are several key reasons why these services are indispensable:
Cyber Threat Assessment: The threat landscape is constantly evolving, with new vulnerabilities and attack vectors emerging regularly. VAPT provides a thorough assessment of potential threats, enabling organizations to identify and mitigate risks before they can be exploited by malicious actors.
Compliance and Regulatory Requirements: Regulatory compliance is a critical aspect of modern business operations. Many industries are governed by regulations that mandate regular security assessments. For instance, the General Data Protection Regulation (GDPR) requires organizations to protect the personal data of EU citizens. VAPT services help organizations meet these compliance standards, avoiding hefty fines and legal consequences.
Protecting Customer Data: The protection of customer data is paramount, especially in industries such as healthcare, finance, and eCommerce. Data breaches can lead to significant financial losses, legal liabilities, and damage to an organization’s reputation. VAPT help safeguard customer information by identifying and addressing vulnerabilities that could lead to data breaches.
Business Continuity and Reputation: A successful cyber-attack can disrupt business operations, leading to downtime, loss of revenue, and damage to an organization’s reputation. VAPT play a crucial role in preventing such incidents, ensuring business continuity, and maintaining customer trust.
Key Components of VAPT
VAPT encompass two primary components: Vulnerability Assessment and Penetration Testing. Each plays a crucial role in identifying and mitigating security risks.
Vulnerability Assessment
Vulnerability Assessment focuses on identifying and evaluating vulnerabilities in systems, networks, and applications. This component includes several key aspects:
- Scanning and Identifying Vulnerabilities: Automated tools are used to scan systems for known vulnerabilities. These scans can detect outdated software, unpatched systems, and misconfigurations.
- Types of Vulnerabilities:
- Software Vulnerabilities: Flaws or weaknesses in software code that can be exploited by attackers.
- Network Vulnerabilities: Weaknesses in network infrastructure, such as open ports, insecure protocols, and improper configurations.
- Human Factors: Risks arising from human errors, such as weak passwords, lack of security awareness, and social engineering.
- Tools and Techniques Used in Vulnerability Assessment: Tools such as Nessus, OpenVAS, and Qualys are commonly used to automate the process of vulnerability scanning. Manual techniques may also be employed to verify and assess vulnerabilities.
Penetration Testing
Penetration Testing involves simulating real-world cyber-attacks to evaluate the security of systems and applications. This component includes several key elements:
- Simulating Cyber-Attacks: Ethical hackers attempt to exploit identified vulnerabilities to understand their potential impact. This helps in assessing the effectiveness of existing security measures.
- Types of Penetration Testing:
- Black Box Testing: Testers have no prior knowledge of the system and attempt to breach security as an outsider would.
- White Box Testing: Testers have full knowledge of the system’s architecture and source code, allowing for a thorough examination.
- Grey Box Testing: Testers have partial knowledge of the system, providing a balanced approach between black box and white box testing.
- Tools and Techniques Used in Penetration Testing: Tools such as Metasploit, Burp Suite, and Nmap are used to identify and exploit vulnerabilities. Penetration testers also use manual techniques to simulate complex attack scenarios and uncover hidden security flaws.
Types of VAPT
VAPT encompass a wide range of testing methodologies, each tailored to specific aspects of an organization’s security. Here are the main types of VAPT :
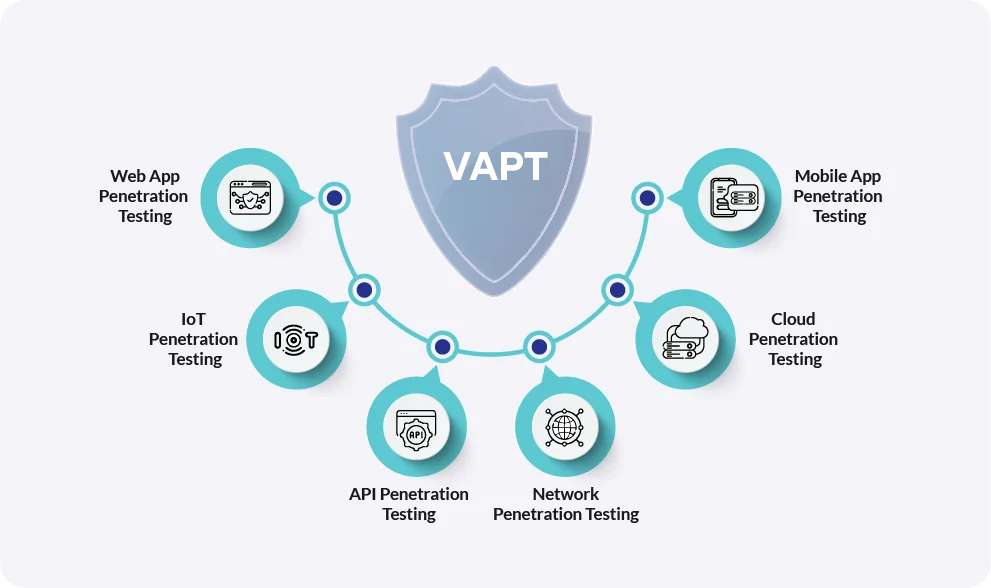
Network Penetration Testing: This type of testing focuses on assessing the security of an organization’s network infrastructure. It involves scanning for vulnerabilities in network devices such as routers, switches, firewalls, and servers. Common issues identified include weak passwords, outdated firmware, and misconfigurations. An example case could involve identifying an exposed management interface on a router that could allow unauthorized access.
Web Application Penetration Testing: Web applications are a common target for attackers due to their accessibility and potential to handle sensitive data. This testing focuses on identifying vulnerabilities such as SQL injection, cross-site scripting (XSS), insecure direct object references, and more. For instance, a penetration tester might discover an XSS vulnerability in a comment section, allowing attackers to inject malicious scripts.
Mobile Application Penetration Testing: With the proliferation of mobile apps, ensuring their security has become crucial. This testing examines mobile apps for vulnerabilities specific to mobile platforms, such as insecure data storage, weak encryption, and improper session handling. For example, an assessment might reveal that a banking app stores sensitive information in an unencrypted format.
Wireless Network Penetration Testing: Wireless networks present unique security challenges due to their inherent nature of transmitting data over the air. This testing evaluates the security of wireless access points, encryption protocols, and network segmentation. An example issue could involve weak WPA2 encryption, allowing attackers to intercept network traffic.
Social Engineering Testing: Human factors are often the weakest link in cybersecurity. Social engineering testing involves simulating attacks that exploit human psychology, such as phishing, pretexting, and baiting. For instance, a tester might send a phishing email to employees, attempting to trick them into revealing sensitive information.
Cloud Security Assessment: As organizations increasingly adopt cloud services, ensuring cloud security is critical. This assessment evaluates the security of cloud platforms, including infrastructure-as-a-service (IaaS), platform-as-a-service (PaaS), and software-as-a-service (SaaS) models. A common issue might involve misconfigured cloud storage buckets that expose sensitive data.
IoT Security Testing: The Internet of Things (IoT) brings unique security challenges due to the diversity and scale of devices. IoT security testing focuses on identifying vulnerabilities in connected devices, such as smart appliances, wearable devices, and industrial control systems. An example issue could involve insecure firmware updates that allow attackers to compromise devices.
Physical Security Testing: Physical security is an integral part of overall cybersecurity. This testing assesses an organization’s physical security measures, such as access controls, surveillance systems, and security personnel. An example case might involve testing the effectiveness of badge systems and locks to prevent unauthorized access.
 VAPT for Different Industries
VAPT for Different Industries
Different industries have unique cybersecurity challenges and requirements. Tailoring VAPT to these specific needs is crucial for effective protection:
VAPT for Small Businesses: Small businesses often operate with limited resources and may lack dedicated cybersecurity teams. VAPT offer a cost-effective solution to identify vulnerabilities and protect against potential threats. For example, a small retail business might use VAPT services to secure its point-of-sale systems and protect customer payment information.
VAPT for Enterprises: Large enterprises have complex IT infrastructures and face a broader range of cyber threats. VAPT for enterprises often include advanced testing methodologies, such as network penetration testing, application security testing, and red teaming. For instance, a multinational corporation might use VAPT to assess the security of its global network and identify potential entry points for attackers.
VAPT for eCommerce: eCommerce platforms are particularly vulnerable to cyber-attacks due to the volume of sensitive customer data they handle. VAPT for eCommerce focus on securing web applications, payment gateways, and ensuring PCI DSS compliance. For example, an online retailer might use VAPT to test for vulnerabilities in its checkout process and prevent credit card fraud.
VAPT for Healthcare: The healthcare industry handles sensitive patient data, making it a prime target for cyber-attacks. VAPT in healthcare focus on safeguarding electronic health records (EHRs), ensuring HIPAA compliance, and protecting against ransomware attacks. For instance, a hospital might use VAPT services to test the security of its patient management systems and prevent data breaches.
VAPT for Financial Institutions: Financial institutions face unique challenges in protecting financial data and preventing fraud. VAPT for this sector include thorough assessments of online banking systems, payment processing networks, and compliance with regulations like PCI DSS and SOC 2. For example, a bank might use VAPT to identify vulnerabilities in its online banking platform and prevent unauthorized access to customer accounts.
VAPT Government Agencies: Government agencies manage critical information and infrastructure, making them prime targets for cyber-attacks. VAPT for government agencies focus on securing sensitive information, protecting against cyber espionage, and ensuring compliance with national cybersecurity standards. For example, a government agency might use VAPT to test the security of its classified information systems and prevent unauthorized access.
Benefits of VAPT
The benefits of VAPT extend beyond mere vulnerability identification. Here are some key advantages:
Identifying and Mitigating Vulnerabilities: VAPT provide a detailed analysis of an organization’s security posture, identifying vulnerabilities and their potential impact. This allows organizations to prioritize and address critical issues, reducing the risk of exploitation.
Enhancing Cybersecurity Posture: Regular VAPT assessments help organizations improve their overall cybersecurity posture. By continuously identifying and addressing vulnerabilities, organizations can stay ahead of emerging threats and reduce the likelihood of successful attacks.
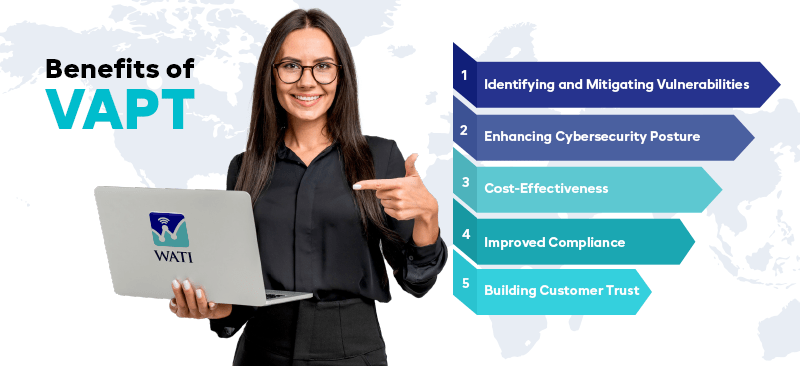 Cost-Effectiveness: While VAPT involves an upfront investment, they can save organizations significant costs in the long run. The potential costs of a data breach, including fines, legal fees, and reputational damage, far outweigh the cost of regular security assessments.
Cost-Effectiveness: While VAPT involves an upfront investment, they can save organizations significant costs in the long run. The potential costs of a data breach, including fines, legal fees, and reputational damage, far outweigh the cost of regular security assessments.
Improved Compliance: VAPT helps organizations meet industry-specific regulatory requirements and standards. By conducting regular assessments and addressing vulnerabilities, organizations can demonstrate compliance and avoid penalties associated with non-compliance.
Building Customer Trust: A robust cybersecurity posture builds customer trust and confidence. Customers are more likely to do business with organizations that prioritize their data security and take proactive measures to protect their information.
VAPT Process: Step-by-Step Guide
The VAPT process involves several key stages, each crucial for a comprehensive assessment:
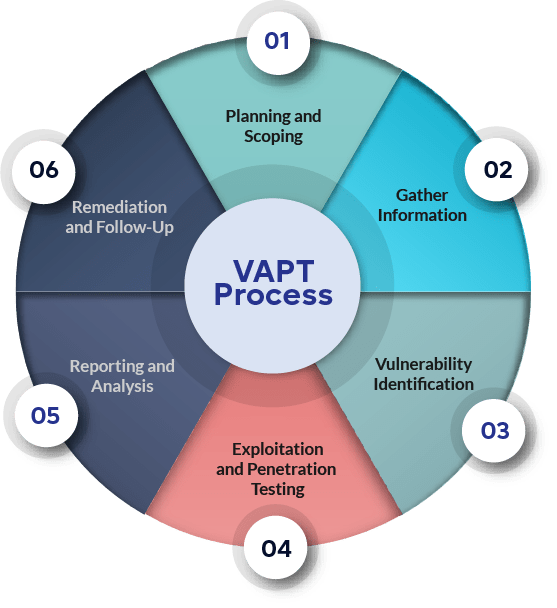
Planning and Scoping: The first stage involves defining the scope of the assessment, including the systems, applications, and networks to be tested. This stage also includes identifying the objectives and goals of the assessment, such as compliance requirements or identifying specific vulnerabilities.
Information Gathering and Reconnaissance: In this stage, the VAPT team collects information about the target systems, applications, and networks. This includes identifying IP addresses, domain names, and potential entry points. The team may also gather information about the organization’s employees, infrastructure, and security measures.
Vulnerability Identification: Using automated tools and manual techniques, the VAPT team identifies potential vulnerabilities in the target systems. This includes scanning for known vulnerabilities, misconfigurations, and weak passwords. The team may also conduct manual testing to identify complex issues that automated tools may miss.
Exploitation and Penetration Testing: In this stage, the VAPT team attempts to exploit the identified vulnerabilities to understand their impact. This involves simulating real-world attacks, such as exploiting a vulnerable web application or gaining unauthorized access to a network. The team documents the findings, including the methods used and the extent of access gained.
Reporting and Analysis: The VAPT team compiles a detailed report outlining the findings of the assessment. The report includes a list of identified vulnerabilities, their severity, and recommended remediation measures. The team may also provide a risk assessment and recommendations for improving the organization’s security posture.
Remediation and Follow-Up: The final stage involves implementing the recommended remediation measures to address the identified vulnerabilities. The VAPT team may provide guidance and support during this stage, including re-testing to ensure that the issues have been resolved. The organization may also conduct follow-up assessments to ensure ongoing security.
VAPT Best Practices
To maximize the effectiveness of VAPT, organizations should follow these best practices:
Regular Assessments: Conduct VAPT assessments regularly, at least annually, or after significant changes to the IT infrastructure. This ensures that new vulnerabilities are identified and addressed promptly.
Comprehensive Scoping: Define a comprehensive scope for the assessment, covering all critical systems, applications, and networks. A well-defined scope ensures that the assessment covers all potential attack surfaces.
Collaboration and Communication: Maintain open communication between the VAPT team and internal stakeholders. This includes sharing information about the organization’s infrastructure, security measures, and potential concerns.
Prioritizing Remediation: Prioritize the remediation of identified vulnerabilities based on their severity and potential impact. Address critical issues first, followed by less severe vulnerabilities.
Continuous Improvement: Use the findings of VAPT assessments to improve the organization’s overall cybersecurity posture. This includes updating security policies, implementing new security measures, and conducting employee training.
Compliance and Regulatory Requirements
Compliance with industry-specific regulations and standards is a critical aspect of VAPT. Here are some common compliance requirements:
GDPR (General Data Protection Regulation): GDPR mandates that organizations protect the personal data of EU citizens. VAPT help organizations identify and address vulnerabilities that could lead to data breaches, ensuring compliance with GDPR requirements.
PCI DSS (Payment Card Industry Data Security Standard): PCI DSS applies to organizations that handle payment card information. VAPT help organizations identify and address vulnerabilities in payment systems, ensuring compliance with PCI DSS standards.
HIPAA (Health Insurance Portability and Accountability Act): HIPAA mandates the protection of patient data in the healthcare industry. VAPT help healthcare organizations identify vulnerabilities in electronic health records (EHRs) and other systems, ensuring compliance with HIPAA requirements.
SOC 2 (Service Organization Control 2): SOC 2 is a framework for managing customer data based on five trust service principles: security, availability, processing integrity, confidentiality, and privacy. VAPT services help organizations identify and address vulnerabilities that could impact these principles, ensuring compliance with SOC 2 standards.
Cost of VAPT
The cost of VAPT services varies based on several factors, including the scope of the assessment, the complexity of the organization’s infrastructure, and the expertise of the VAPT provider. Here are some factors that influence the cost:
Scope and Depth of Assessment: The more comprehensive the assessment, the higher the cost. A thorough assessment that includes multiple types of testing, such as network penetration testing, web application testing, and red teaming, will cost more than a basic vulnerability assessment.
Size and Complexity of Infrastructure: The size and complexity of the organization’s IT infrastructure also impact the cost. Larger organizations with complex networks, numerous applications, and multiple locations may require more extensive testing, resulting in higher costs.
Expertise and Experience of the Provider: The expertise and experience of the VAPT provider also play a role in determining the cost. Providers with a proven track record and specialized expertise may charge higher fees for their services.
Frequency of Assessments: The frequency of assessments also affects the cost. Regular assessments, such as quarterly or semi-annual assessments, may offer cost savings compared to ad-hoc assessments.
Customization and Additional Services: Customization of the assessment and additional services, such as remediation support and follow-up assessments, may also impact the cost.
While the cost of VAPT services can vary, it is essential to consider the potential cost savings from preventing cyber incidents, avoiding regulatory fines, and protecting an organization’s reputation.
VAPT and Cybersecurity Frameworks
VAPT is often aligned with established cybersecurity frameworks and standards. These frameworks provide guidelines for managing and improving cybersecurity practices. Here are some commonly used frameworks:
NIST Cybersecurity Framework: The National Institute of Standards and Technology (NIST) Cybersecurity Framework provides a comprehensive set of guidelines for managing cybersecurity risks. VAPT align with the framework’s “Identify” and “Protect” functions, helping organizations assess vulnerabilities and implement security controls.
ISO/IEC 27001: ISO/IEC 27001 is an international standard for information security management systems (ISMS). VAPT help organizations identify vulnerabilities and implement controls to achieve compliance with ISO/IEC 27001 requirements.
CIS Controls: The Center for Internet Security (CIS) Controls provides a set of best practices for securing IT systems and data. VAPT help organizations implement and validate controls, such as secure configuration, vulnerability management, and incident response.
OWASP Top Ten: The Open Web Application Security Project (OWASP) Top Ten is a list of the most critical web application security risks. VAPT help organizations identify and address these risks, ensuring the security of web applications.
How to Choose a VAPT Service Provider
Selecting the right VAPT service provider is crucial for a successful assessment. Here are some factors to consider when choosing a provider:
Experience and Expertise: Look for a provider with extensive experience in VAPT services. Consider their track record, industry expertise, and the qualifications of their team members.

Certifications and Credentials: Ensure that the provider’s team members hold relevant certifications, such as Certified Ethical Hacker (CEH), Offensive Security Certified Professional (OSCP), or Certified Information Systems Security Professional (CISSP).
Reputation and Reviews: Research the provider’s reputation and customer reviews. Testimonials, case studies, and references can provide valuable insights into their reliability and effectiveness.
Comprehensive Service Offerings: Choose a provider that offers a wide range of services, including vulnerability assessment, penetration testing, red teaming, and more. This ensures that all aspects of your security are covered.
Communication and Reporting: Clear communication and detailed reporting are essential for understanding the assessment’s findings and implementing remediation measures.
Future Trends in VAPT
The field of VAPT is constantly evolving, with new technologies and methodologies emerging. Here are some trends shaping the future of VAPT:
Automation and AI: The use of automation and artificial intelligence in VAPT is increasing. These technologies can help identify vulnerabilities faster and more accurately, allowing for more efficient assessments. AI-powered tools can analyze vast amounts of data, detect patterns, and identify anomalies that may indicate potential security threats.
Evolving Cyber Threat Landscape: As cyber threats continue to evolve, so do the techniques and tools used in VAPT. Organizations must stay updated with the latest trends and threats to ensure effective cybersecurity. This includes staying informed about new attack vectors, emerging vulnerabilities, and advanced persistent threats (APTs).
Importance of Threat Intelligence: Integrating threat intelligence into VAPT services provides valuable insights into emerging threats and vulnerabilities. Threat intelligence helps organizations understand the tactics, techniques, and procedures (TTPs) used by attackers, allowing for more effective defenses.
Focus on Cloud Security: As more organizations move to the cloud, ensuring cloud security becomes increasingly critical. Future VAPT will place greater emphasis on assessing cloud configurations, securing cloud-native applications, and evaluating the security of cloud service providers. This includes examining cloud infrastructure, services, and data storage to ensure robust security measures are in place.
Enhanced Mobile and IoT Testing: With the proliferation of mobile devices and IoT technologies, VAPT is expected to enhance its focus on these areas. Mobile and IoT security assessments will become more sophisticated, addressing emerging vulnerabilities and ensuring that these devices and applications are adequately protected against cyber threats.
Integration with DevSecOps: The integration of security into the development process, known as DevSecOps, is becoming a key trend. VAPT will increasingly work with development teams to ensure security is embedded throughout the software development lifecycle (SDLC). This approach allows for the early identification of vulnerabilities and the implementation of security measures from the outset.
Increased Emphasis on Social Engineering: As social engineering attacks become more sophisticated, VAPT will place a greater emphasis on testing an organization’s resilience to such threats. This includes conducting simulated phishing attacks, pretexting scenarios, and other social engineering tactics to assess employee awareness and response.
Regulatory and Compliance Focus: With the growing number of regulations and compliance requirements, VAPT will continue to align with various standards and frameworks. This includes ensuring that assessments meet the requirements of regulations such as GDPR, PCI DSS, HIPAA, and SOC 2, and helping organizations stay compliant with evolving standards.
Collaboration with Managed Security Service Providers (MSSPs): Organizations are increasingly relying on Managed Security Service Providers (MSSPs) for ongoing security management. VAPT will likely collaborate more with MSSPs to provide integrated solutions that combine regular assessments with continuous monitoring and incident response.
Conclusion
In today’s digital age, safeguarding your organization against cyber threats is more important than ever. Vulnerability Assessment and Penetration Testing (VAPT) play a crucial role in identifying and addressing security weaknesses, ensuring compliance with regulatory standards, and protecting sensitive data. By understanding the various types of VAPT, their benefits, and best practices, organizations can take proactive steps to enhance their cybersecurity posture.
Regular VAPT assessments, tailored to the specific needs of your organization and industry, provide valuable insights into potential vulnerabilities and offer actionable recommendations for remediation. Whether you are a small business, a large enterprise, or an organization in a specialized industry, VAPT services can help you stay ahead of emerging threats and protect your critical assets.
To ensure your organization is well-protected against cyber threats, consider engaging with a reputable VAPT service provider. By conducting regular assessments and addressing identified vulnerabilities, you can enhance your cybersecurity posture, comply with regulatory requirements, and build trust with your customers.
If you’re ready to take the next step in securing your organization, contact us today to learn more about our comprehensive VAPT services and how we can help you safeguard your digital assets.




