2022: A COMPLETE GUIDE TO
Cloud data breaches have become a common occurrence. Billions of customer records have been exposed in just the last 12 months alone. Industry experts have projected matters to continue to get much worse. How did we get here?
Public Clouds ushered in an era of unprecedented agility. Naturally, organizations of every size are adopting the cloud and making it a mainstay of their infrastructure. The explosive growth of the cloud bears a close resemblance to its previous cousin – the Internet.
Most successful attacks on cloud services involve the exploitation of various misconfigurations. To keep up the insatiable user demand, Cloud Providers are adding more services at a dizzying pace, with each new service coming with its own set of access and security configurations. Imagine the complexity involved in keeping tabs on all the configurations across all of those services, from multiple cloud providers, who are constantly updating and releasing services. Additionally, regulators bring out a swath of regulatory frameworks with frequent revisions that do not help any. All of these forces together make cloud security incredibly complex. As this requires a multitude of skills, it is proving to be an impossible task for the vast majority of organizations.
This guide explains who is responsible for cloud security, between cloud providers and cloud users, and explores different approaches, tools and service models available for cloud security.
What is Cloud Security?
Cloud security breaches come in many forms, like data leakage, access compromise, privilege misuse, and malicious attacks (malware, DoS, etc). Just like information security (infosec) and network security, cloud security is also about ensuring the security of hosted services on the cloud over the internet, with a combination of –
Technical Controls
Policy & Standards as Controls
Procedures & Services as Controls
Download The Complete Guide
Who is Responsible for Cloud Security?
Most Cloud Users mistakenly assume that Cloud Providers would be responsible for “entire” cloud security. That’s flawed complacency. Cloud Providers do carry responsibility for some parts of the cloud (‘security of the cloud’) and Cloud Users are responsible for the rest (‘security in the cloud’). It has been reported that in the vast majority of the data breaches, if not in all of them, Cloud Providers have not been technically at fault, but rather were the result of some or other security or access misconfigurations set up by Cloud Users. The graphic below describes the responsibility matrix between Cloud Providers and various types of Cloud Users.
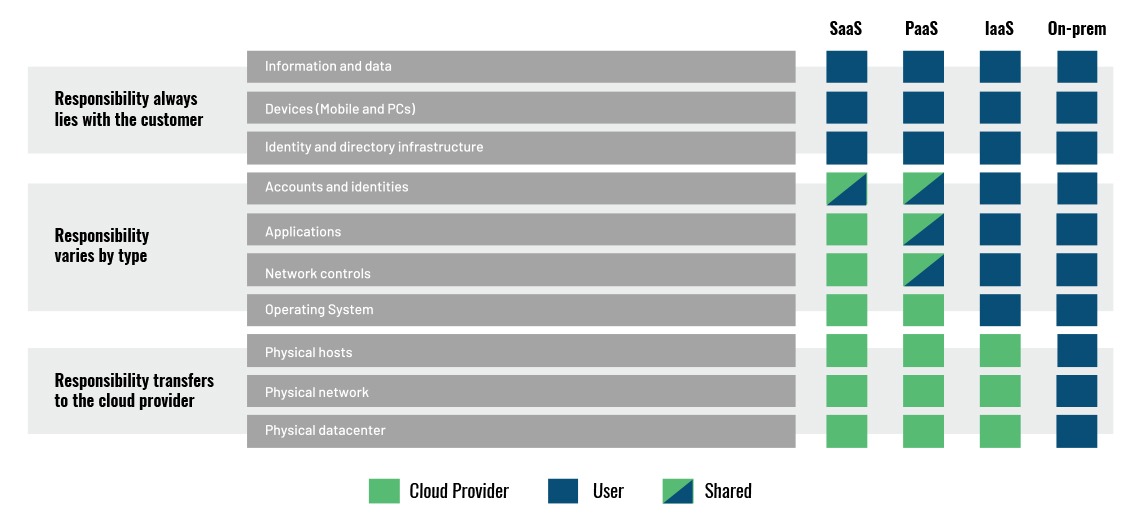
The accountability, ownership & responsibility map to the level of access the actors have over the cloud stack, and widely vary based on the service model adopted by the organization as part of the cloud adoption.
Software as a Service (SaaS)
The cloud provider is responsible for most of the security (perimeter security, logging/monitoring/auditing, and application security), while the cloud users are accountable for just access authorization and entitlements privileges.
Platform as a Service (PaaS)
Responsibility is more evenly split among this model, with cloud users being responsible for everything they implement on the platform while cloud providers are accountable for the security of the platform. For example, when using a database as a service, the cloud provider manages fundamental security, patching, and core configuration, while the cloud user is responsible for everything else, including which security features of the database to use, managing accounts, or even authentication methods.
Infrastructure as a Service (IaaS)
This places a higher responsibility on the cloud user for the security of everything above hypervisor/virtual machines. Just like PaaS, the provider is responsible for the foundational security of the cloud platform, while the cloud user is responsible for everything they build on the infrastructure. For example, the IaaS provider will likely monitor their perimeter for attacks, but the consumer is fully responsible for how they define and implement their virtual network security, based on the tools available on the service.
These roles are further complicated when using cloud brokers or other intermediaries and partners. The most important security consideration is knowing exactly who is responsible for what in any given cloud project. Nevertheless, data, endpoints, account and access management are always the responsibility of cloud users, regardless of the type of deployment.
Cloud is Security’s new Achilles Heel?
Cloud providers apply extraordinary care to secure their offerings. Yet, cloud breaches keep happening more frequently. It is reported that some of the largest cloud breaches at companies Capital One were due to simple configuration mistakes. How did cloud become the Achilles heel for an organization’s security posture?
1) Complexity Overdose
Cloud computing heralded a seismic shift in IT environments, enabling users to spin up infrastructure instantly, deploy applications in a flash, and scale the infrastructure with just a few clicks. It’s no surprise organizations of all sizes are making cloud a mainstay of theirs, driving cloud adoption at an exponential pace.
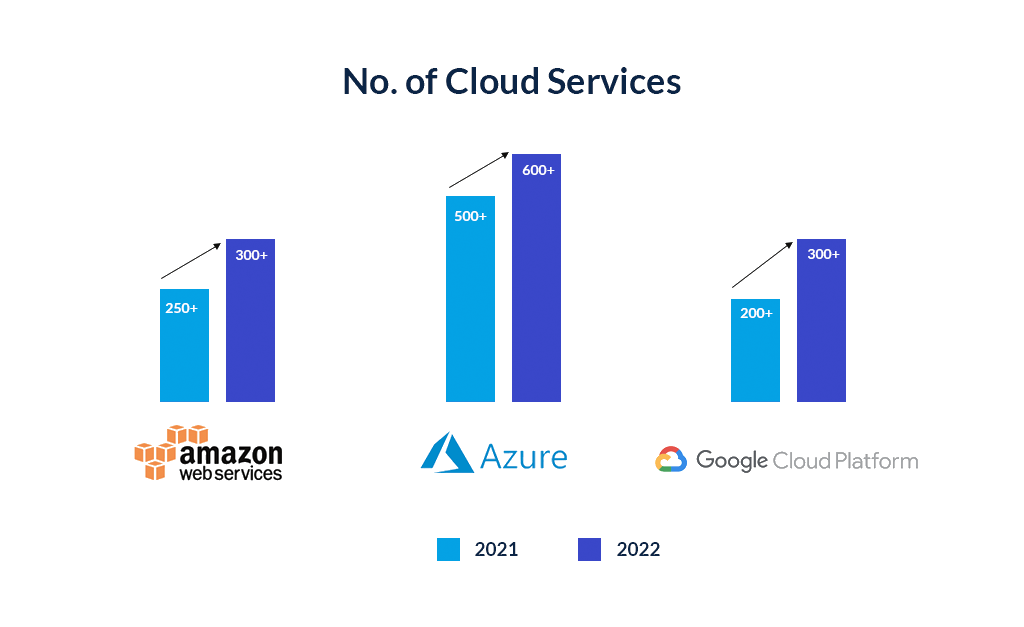
To keep with the demand, cloud providers are responding with an avalanche of new services. The big three – AWS, Azure and GCP – offer several hundreds of different services for compute, storage, AI, security, database, analytics, networking, mobile, IoT, and a lot more. Each of them comes with its own unique settings, granular configurations, and authorization policies that make it exceptionally hard to maintain security posture.
2) Blistering pace of new Cloud Services
While cloud providers, especially the big three, are flourishing with breakneck growth of customers and revenues from the cloud, there is intense competition among themselves and with new market entrants like Oracle, Alibaba, IBM, etc. To stay competitive, all cloud providers are constantly releasing new services and updating new features. The blistering pace of change is making it near-impossible for cloud users to keep up. This overwhelming complexity has a debilitating effect on IT administrators. Just simple configuration errors or one-click mistakes that are not caught in time can result in organization-wide data breaches.

3) Multi-Cloud is becoming normal
Multi-cloud is fast emerging as the new normal for organizations, owing to the advantages of increased agility, best-of-the-breed, costs, geographic coverage, avoidance of vendor lock-in, avoiding a single point of failure, etc. Even similar services of different cloud providers carry different settings and configuration parameters. The advent of multi-cloud has compounded difficulty for administrators who are struggling to gain a grip of just one cloud environment before.
4) Regulatory Compliance
Organizations that deal with sensitive and personal data are subject to stringent regulatory compliance, which in itself keeps changing frequently. While cloud providers are usually compliant at their level, it is incumbent upon cloud users to deploy cloud services in a specific way to stay compliant with the laws and regulations.
5) Cloud Security skills are woefully short
While the increased complexity of the cloud is overwhelming for administrators, technical organizations have battles of their own. Most developers and IT professionals do not possess adequate security-related skills, much less cloud security knowledge. This is true even with brilliant and experienced teams working on leading-edge technologies. Most organizations have developers operating in the cloud environment, who not being cloud security experts, tend to make configuration changes to the cloud without a full grasp of the ramifications of those changes.
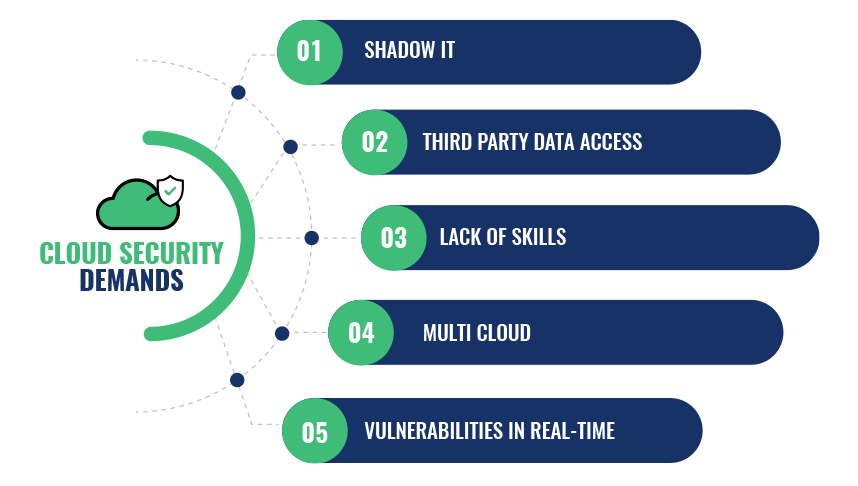
With the lack of visibility and control over ever-changing configurations, it’s no surprise that cloud data breaches and exposures are so rampant.
Cloud security is to ensure avoidance & mitigation of risks by running effective security programs inclusive of security controls and procedures.
Download The Complete Guide
Approaches for Cloud Security
There are several approaches for cloud security, with no one single approach being the best or universally suitable for all organizations. The size of the cloud footprint, type of business domain, availability of skilled resources, and budgets together play a vital role in determining which approach is the best fit.
I. Manual auditing
Internal security teams or a third party perform manual security audits, which involve vulnerability scans and assessing permissions and policies. Regular audits can help identify anomalies and establish a baseline for security practices. Many organizations tend to perform security audits at least once or twice a year. One of the limitations of manual auditing – particularly when they are not regularly performed – is that months of harmful activities may have already occurred.
II. Scripts and Opensource tools
As organizations ramp up cloud adoption, manual auditing alone is inadequate. Automation is called for to handle frequent reviews for larger footprints. Many teams build homegrown scripts to automate the review process. Places like Github provide a wide range of prebuilt scripts, which are available for teams to download and customize for their specific needs. For those looking for further automation (beyond scripting), there is a wide choice of opensource tools, that provide broader review functionality for detecting weak points, reviewing the results, and implementing changes.
Best Practices and Tools
Some of the Opensource tools

III. Native security tools of cloud providers
Not just the big three, all major cloud providers invest significant resources in keeping their platform secure enough. As cloud security is a shared responsibility, cloud providers offer a range of security tools for their users to stay secure. Cloud providers’ tools come with better visibility, and essentially leave the security aspect to cloud users’ knowledge on cloud configuration settings. Therein lies the central challenge. With so much change happening constantly in cloud services, new features, each with its own set of complex configuration settings, it’s near impossible for cloud administrators to maintain the overall security posture. Besides, multi-cloud is a new norm in most organizations, so cloud providers’ individual native security tools can compound the complexity. But for organizations that are mostly invested in one cloud provider, it’s usually a good place to start with their native security tools.

IV. Continuous auditing
Each of these approaches described above come with limitations. Continuous auditing can provide full visibility, automation, and even remediation to address the problem efficiently, especially as cloud footprints grow. This entails ongoing monitoring with reporting on the state of security of your environment, based on any change from the state that you set with your security controls. Continuous cloud security monitoring is an area of intense research activity, with a wide range of approaches. The following are major categories of the tools, each offers its own merits and drawbacks.
CASB (Cloud Security Access Broker)
CASB is software (on cloud or on-premises) that monitors user activities and enforces the security compliance policies between users and cloud applications. CASB extends the visibility and controls of the organization, by leveraging network firewalls, Web Application Firewalls (WAF), authentication, and Data Loss Prevention (DLP) technologies.
Leading CASB vendors

CWPP (Cloud workload protection platforms)
CWPP helps organizations to have the controls to ensure workloads are deployed in the right place and have appropriate security measures. CWPP consolidates management and provides visibility of cloud resources across multiple cloud providers in a single console. CWPP performs security functions like hardening, vulnerability scanning and remediation, network segmentation, system integrity checks, and application whitelisting.
Leading CWPP vendors

CSPM (Cloud Security Posture Management)
CSPM is a cloud security category designed to automate security and compliance and provide control over cloud infrastructure configuration. CSPM solutions operate at the cloud provider control plane level and leverage APIs from the underlying cloud vendor, to validate hundreds of settings across regions and accounts. CSPM is commonly provided as a cloud service.
Leading CSPM vendors

CNAPP (Cloud-Native Application Protection Platform)
CNAPP combines the capabilities of CWPP and CSPM, scans workloads and configurations in development and protects them at runtime. CNAPP tools provide unified visibility for SecOps and DevOps teams. Particularly relevant for identifying, assessing, prioritizing, and adapting to risk in cloud-native applications, infrastructure, and configuration that require a zero-trust security posture. Having separate CWPP and CSPM tools for the same teams means unnecessary overhead, it makes sense to consider CNAPP solution instead.
Leading CNAPP vendors

Leading CNAPP vendors

Which Tool to use? The selection of the tool
depends on the organization’s priorities.
- CASB is probably the best option if the primary concern is to control enterprise cloud usage.
- CWPP is perhaps a better choice, to protect its workloads on the cloud and reinforce application security.
- CSPM is a recommended choice for enforcing compliance with cloud configuration best practices.
- CNAPP makes sense for the organisations that are rapidly expanding cloud footprints.
V. SECaaS (Cloud Security as a Service)
The myriad of tools and approaches can be overwhelming for internal teams with the need for a broad set of skills. As a result, Security as a service outsourcing solution is becoming increasingly popular as they augment the in-house security team’s skills and scale security needs with the business needs. Offered as a managed service, it can be scaled up or down as per the organization’s evolving needs.
Download The Complete Guide
Cloud Security Frameworks
Taking a leaf from information security (InfoSec) standards by various industry bodies, Cloud Security too attracted a great deal of standardization as implementable frameworks by various organizations. Some of the most popular ones are listed here:
Apart from these, there are other industry-specific security standards, such as:
1) FedRAMP (for doing business with any US Federal agencies)
2) PCI/DSS (Ecommerce and online payment processing)
3) HIPAA (for healthcare information of individuals)
Summary
Rapid cloud adoption is here to stay and so is its associated ever-increasing complexity. Businesses need a better understanding of the risks they face with cloud security. However, many organizations struggle to find the right approaches to adequately address them. This guide provides a high-level blueprint of different approaches for addressing an organization’s cloud security threats.
Cloud Security awareness would play a significant role in any cyber security program. This guide aims at filling the gap for the industry leaders and the team on the ground as a holistic reference on key areas of cloud security.
At WATI, we have recently conducted a webinar on Cloud Security or Lack of It: Threat Vector #1.
This webinar explains cloud security, division of responsibility between Cloud Providers and Cloud Users, and outlines different approaches, tools, and service models available. WATI’s cybersecurity experts will provide insights on how cloud exploits typically happen and cover critical protection points in your cloud attack surface. Watch the webinar recording here.